When we talk about cybersecurity for small businesses, what do we really mean? Simply put, it's all about protecting your company's digital lifeblood—everything from your computers and network to your precious data—from being stolen, damaged, or held for ransom. It’s a mix of smart strategies, the right tools, and good old-fashioned best practices designed to keep cyber attackers at bay.
And believe me, they are a very real and growing threat for businesses just like yours.
Why Your Small Business Is a Prime Target for Cyber Attacks
There's a dangerous myth doing the rounds: that cybercriminals only go after the big fish, the giant corporations with endless cash reserves. The truth is, small and medium-sized enterprises (SMEs) aren't just getting caught in the crossfire; they're often the main target. Why? Because criminals are betting that you're an easier score.
Imagine your business is a shop on the local high street. A massive corporation is like a fortress with steel shutters, on-site guards, and a high-tech alarm system. In contrast, many small businesses, without realising it, leave the back door unlocked overnight. Attackers count on this, exploiting that common "we're too small to be a target" mindset. This, combined with tight budgets and a lack of dedicated security expertise, creates the perfect storm for a cyber attack.
The Misconception of Anonymity
It's easy to think your business flies under the radar. But most cyber attacks today are automated. Bots and malicious scripts are constantly sweeping the internet, not looking for company logos or big names, but for specific vulnerabilities—like a plugin that needs updating or a password that's too simple. Your business isn't targeted because of who you are; it's targeted because it has an unprotected digital door.
These attacks aren't always about landing one huge payday, either. More often, it’s a numbers game. Criminals will hit thousands of smaller businesses for relatively modest amounts. This approach is far less likely to trigger a major law enforcement response, but when added up, it's incredibly profitable for them.
A single breach can be devastating. It's not just about the immediate financial loss; it's the erosion of customer trust, the crippling downtime, and the potential regulatory fines that can truly hurt. For an SME, the road to recovery can be a steep one, which is why a proactive defence is your best investment.
You Are a Gateway to Bigger Targets
Sometimes, your business isn't the end game—it's just a stepping stone. Cybercriminals might target you specifically to get to a bigger company in your supply chain, like a major client or a key supplier you work with closely. By getting inside your network, they can piggyback on your trusted relationship to launch an even bigger attack on their real target.
This tactic, known as a supply chain attack, is becoming more and more common. Your company might hold sensitive client data or have network permissions that make you a very tempting backdoor into a much larger, more secure system. Suddenly, your business is an unwilling accomplice, facing your own damages plus severe reputational and legal fallout.
The threat isn't going away; it's growing. Recent statistics show that a staggering 81% of UK businesses hit by cyber attacks are SMEs, with the average financial blow landing at £4,200. What’s truly alarming is that an estimated 97% of these incidents could have been stopped with modern security measures, proving that taking action is incredibly effective. You can learn more by reviewing the latest UK cyber crime statistics.
Recognising the Top Threats to Your Business
To build a solid defence, you first need to know what you’re up against. Improving your cybersecurity for small businesses isn't about getting tangled in complex technical terms; it's about understanding the real-world dangers that could disrupt your operations.
These aren't just random bits of digital bad luck. They are targeted attacks that zero in on common business weaknesses, and unfortunately, small businesses are often seen as easy targets. Getting to grips with these primary threats is the most important first step you can take.
Phishing: The Deceptive Lure
Phishing is the most common threat for one simple reason: it goes after your most unpredictable asset—your people. It’s a bit like a con artist sending a convincing but fake delivery notice to your reception. The email looks official and asks your staff to click a link to "confirm a delivery slot," but that one click is all it takes to install harmful software or steal their login credentials.
That’s phishing in a nutshell. It uses sneaky emails, texts, or messages that look like they’re from a trusted source—your bank, a supplier like Royal Mail, or even a manager. The aim is always to trick someone into giving away sensitive information like passwords and financial details, or to open the door for malware. You can find more practical advice in our guide on protecting against phishing email scams.
Ransomware: The Digital Hostage Taker
Imagine a criminal breaking into your office, not to steal anything, but to lock every single filing cabinet and then demand a hefty fee for the keys. That's exactly what ransomware does to your digital files. Once a hacker gets into your network—often through a clever phishing email—they encrypt everything that matters.
Your customer lists, financial records, and crucial project files become completely unusable. Soon after, a ransom note pops up on your screen demanding payment (usually in cryptocurrency) for a decryption key. Paying up is a huge gamble; there's no guarantee you'll get your data back, and it flags you as an easy target for future attacks. Even without paying, the downtime alone can be crippling, halting your business for days or weeks.
Data Breaches: The Silent Theft
A data breach isn't a loud smash-and-grab. It’s more like a corporate spy who slips in unnoticed, photocopies all your confidential client files and employee records, and then vanishes without a trace.
You might not even realise it's happened for weeks or months, until that stolen data is used for identity theft or sold online. The fallout can be devastating, from massive fines under GDPR to a complete loss of customer trust that’s incredibly difficult to win back.
To put these dangers into perspective, here's a quick breakdown of common threats and what they could mean for your business.
Common Cyber Threats and Their Impact on SMEs
| Threat Type | How It Works (Simplified) | Potential Business Impact |
|---|---|---|
| Phishing | Scammers send fake emails or messages to trick employees into giving away passwords or clicking malicious links. | Can lead to data breaches, ransomware infections, financial loss, and unauthorised access to company accounts. |
| Ransomware | Malicious software encrypts all your files, making them inaccessible until a ransom is paid to the attackers. | Complete business shutdown, significant financial loss (from ransom and downtime), and potential permanent data loss. |
| Data Breach | An unauthorised person gains access to and steals sensitive company or customer information. | Severe reputational damage, loss of customer trust, hefty regulatory fines (e.g., GDPR), and potential legal action. |
This table shows just how easily a single click or a weak password can spiral into a major business crisis. Understanding this link is key to building an effective defence.
The image below paints a clear picture of the reality facing small businesses, showing just how common attacks are and how unprepared many businesses remain.
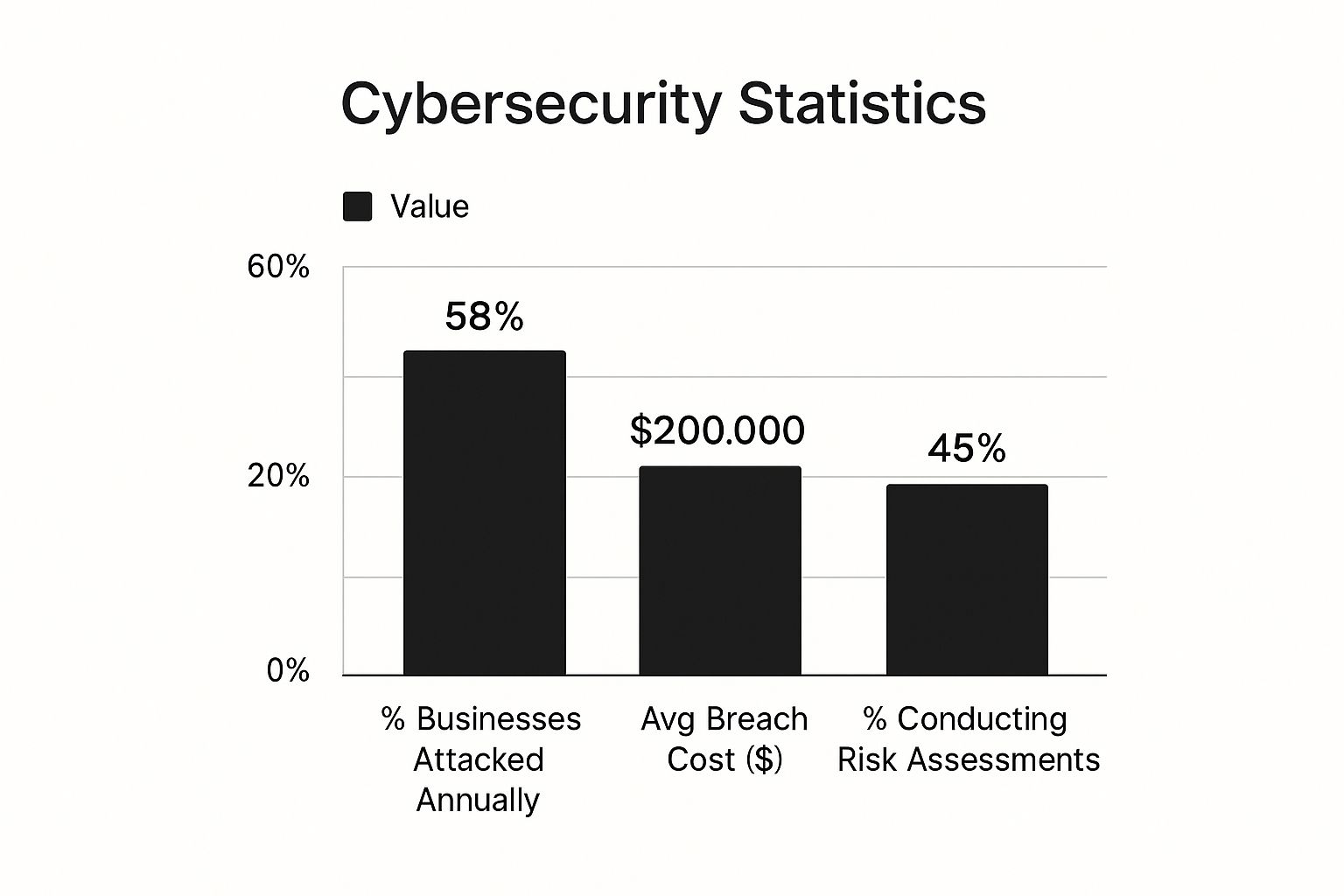
The data speaks for itself. While attacks are frequent, far too few businesses are taking the basic step of assessing their risks. Getting your head around these three core threats—phishing, ransomware, and data breaches—is the foundation of building a truly resilient security posture.
Building Your First Line of Digital Defence

Now that you can spot the main threats, it’s time to put up your first barriers. Think of these as the essential locks and alarms for your digital premises. The good news? You don’t need a massive budget or a full-time IT team to make a real difference. The key is starting with a few high-impact habits.
This isn't about becoming a security guru overnight. It's about taking practical, sensible steps that give you the biggest bang for your buck. Let's walk through a straightforward checklist to build a much stronger defence.
Fortify Your Digital Doors
Your passwords are the keys to your entire business. Weak ones are like leaving your office keys under the doormat for anyone to find. In fact, a staggering 80% of all hacking incidents involve weak or stolen passwords, making this the most critical area to tackle first.
The goal isn't just a strong password; it's a unique password for every single account. That way, if one service gets breached, criminals can't use that same password to unlock your email, banking, and social media.
A password manager is your best friend here. These tools create and remember long, unique passwords for every site you use, meaning you only have to remember one master password.
Next up is Multi-Factor Authentication (MFA). You absolutely must enable it wherever it’s offered. MFA is like adding a deadbolt to your front door; even if a thief steals your key (password), they can't get in without a second piece of information, like a code sent to your phone. Despite its power, a mere 20% of small businesses use it, leaving a huge security gap wide open.
Keep Your Software Updated
Ignoring software updates is like noticing a cracked window in your office and deciding to fix it later. It's a visible vulnerability that attackers are actively looking for. Those update notifications you might be tempted to dismiss often contain vital security patches that mend these "cracked windows" before a digital burglar can climb through.
This rule applies to everything connected to your business network:
- Operating Systems on your computers (e.g., Windows, macOS)
- Web Browsers (e.g., Chrome, Firefox, Safari)
- Business Applications like your accounting software or CRM
- Website Software (e.g., WordPress, plugins, themes)
The easiest way to stay on top of this is to set your devices and software to update automatically. This simple action closes security holes as soon as fixes are released, drastically cutting your risk without any extra effort. For cloud tools like Microsoft 365, it’s just as important to ensure your security settings are correctly configured. You can find out more on our guide to Office 365 cyber security.
Secure Your Wireless Network
Your office Wi-Fi is another major entry point. An unsecured network is like broadcasting an open invitation for anyone nearby to snoop on your activity or try to access your systems.
Start by changing the default admin name and password on your router – the factory settings are often public knowledge and are the first thing an attacker will try. Next, make sure your network is protected with strong encryption; look for the WPA3 or WPA2 setting. It's also smart to set up a separate guest network for visitors. This keeps them off your main business network, where all your sensitive data lives.
A complete defence also considers more advanced measures. For those worried about highly sophisticated threats, exploring electronic surveillance defense strategies provides deeper insights into protecting sensitive business communications.
By focusing on these three core areas—strong passwords with MFA, consistent updates, and a secure Wi-Fi network—you establish a powerful first line of defence. These actions are the bedrock of good cybersecurity for small businesses, transforming your company from an easy target into a much tougher one.
Choosing the Right Security Tools for Your Budget

With a solid set of security habits in place, it’s time to back them up with the right technology. Stepping into the world of security software can feel a bit daunting, but don’t worry—this isn't about buying every expensive gadget on the shelf. It’s more like putting together a starter toolkit. You just need a few reliable, effective tools that get the job done without an enterprise-level price tag.
The goal here is smart investment, not just spending. For most small businesses, the path is already well-trodden. A recent survey highlighted the top four tools being picked up by SMEs: antivirus software (58%), firewalls (49%), VPNs (44%), and password managers (39%). This gives us a brilliant, real-world roadmap of what to prioritise.
This section will walk you through picking these essentials, focusing on what genuinely matters for a small business: ease of use, the ability to grow with you, and overall value.
Prioritise Your Core Security Toolkit
Think of your security technology in layers. Each tool has its own specific job, and when they work together, they create a defence that is far stronger than the sum of its parts. Let's break down the must-have components for any small business and what to look for when you're choosing.
Essential Cybersecurity Tool Comparison for Small Businesses
To get started, it helps to understand what each fundamental tool does and why it's important. The table below breaks down the core functions of the must-have software categories for any small business.
| Tool Category | Primary Function | Key Features to Look For |
|---|---|---|
| Next-Generation Antivirus (NGAV) | Protects endpoints (PCs, laptops) from malware like viruses, ransomware, and spyware. | Real-time threat detection, low system impact (doesn't slow you down), automatic updates, and web protection to block malicious sites. |
| Firewall Protection | Acts as a gatekeeper for your network, monitoring traffic and blocking unauthorised access. | Can be hardware or software-based; look for simple configuration rules and clear activity logs. |
| Data Backup & Recovery | Creates secure copies of your data so you can restore it after a disaster, like a ransomware attack or hardware failure. | Automated cloud backups, strong encryption (both in transit and at rest), and versioning (so you can roll back to a clean file). |
These three tools—NGAV, a firewall, and a backup solution—form the bedrock of your technological defences. Getting these right is the most important first step.
Selecting Tools That Grow with You
As you start comparing different products, it's easy to get bogged down in technical jargon. My advice? Sidestep the complicated spec sheets and focus on practical features that will make your life easier and ensure your investment pays off.
A critical mistake I see time and again is businesses investing in a complex security system that no one on the team truly understands. An easy-to-use tool that is correctly configured and consistently used will always be more effective than an advanced system that's poorly managed.
When you’re weighing up your options, keep these four things at the top of your list:
- Ease of Use: Does the tool have a clean, straightforward interface? You and your team should be able to see what’s going on at a glance without needing a degree in IT.
- Scalability: Will this solution grow with you? Look for a provider that makes it simple to add more users or devices as your company expands. You don’t want to have to switch systems just because you hired two new people.
- Customer Support: When something goes wrong—and sooner or later, it will—you need reliable help, fast. Check what kind of support is on offer. Do they have phone, email, or live chat support that fits your working hours?
- Value for Money: The cheapest option is rarely the best, but the most expensive isn't always necessary either. Aim for that sweet spot: a balance of essential features at a price that fits your budget. Many providers offer security suites that bundle these tools together, which can be very cost-effective for SMEs.
Here is the rewritten section, designed to sound like an experienced human expert.
Turning Your Team into a Human Firewall
All the security software in the world can only do so much. At the end of the day, your strongest line of defence—and the one attackers target most often—is your people. Every single person on your team, from the front desk to the stockroom, makes dozens of small decisions every day that can either protect the business or swing the door wide open for a cybercriminal.
This is why building a security-conscious culture is probably the single most effective thing you can do for your company's safety. When you give your staff the knowledge and instil the right habits, you create what we call a human firewall. This isn't about turning everyone into a tech wizard. It’s about creating a shared sense of awareness, where spotting something that looks a bit 'off' becomes second nature. Your team transforms from a potential vulnerability into your most powerful security asset.
Building Security Awareness Through Training
A strong human firewall is built on continuous training. A quick chat during someone's induction week just won't cut it. Security has to be an ongoing conversation, not a one-time lecture that everyone forgets. The real goal is to make the training engaging, relevant, and easy to remember.
Recent findings from the UK’s Department for Science, Innovation, and Technology really drive this point home. While a staggering 43% of UK businesses reported a cyber breach, there are still huge gaps in staff training and even board-level engagement. It's a persistent problem that shows just how vital it is for small businesses to invest in their people. You can dig deeper into these numbers in the latest UK cybersecurity survey report.
So, how do you make training stick? Here are a few things that actually work:
- Regular, Bite-Sized Reminders: Forget long, boring annual seminars. Try sending out short weekly or monthly security tips by email. Focus on one simple topic at a time, like how to spot a dodgy link or create a better password.
- Use Real-World Examples: Show your team actual phishing emails or social media scams that are doing the rounds. When the threat feels real and immediate, the lessons are far more powerful.
- Interactive Sessions: Hold short, informal catch-ups to chat about recent threats or review a security policy. Make it a safe space where people can ask questions or even admit they clicked on something without fear of being blamed.
Testing and Reinforcing What They've Learnt
Training is only half the battle. You need to know if the information is actually sinking in and being used. This is where a bit of testing comes in handy, giving you a safe way to see how aware your team really is and where you might need to offer more support.
Simulated phishing tests are an incredibly effective tool. You send a harmless, fake phishing email to your team and see who clicks. This isn't about catching people out or naming and shaming. It’s a powerful, hands-on learning moment that demonstrates just how convincing these scams can look in a busy inbox.
When someone does click, it’s a golden opportunity. Follow up with immediate, non-judgemental feedback, pointing out the red flags they missed. A potential mistake is instantly transformed into a valuable, lasting lesson.
Setting Clear Ground Rules for a Secure Workplace
Alongside training, you need clear and simple policies. Think of them not as dense legal documents, but as straightforward guides that set expectations for how everyone should handle company data and equipment. They need to be easy to read and understand.
Start by creating policies for these two key areas:
- Acceptable Device Usage: Lay out the ground rules for using company laptops, phones, and tablets. Be specific about what personal use is allowed (if any) and make it clear that installing unauthorised software is a no-go.
- Data Handling and Access: Clearly define what you consider sensitive information (like customer details or financial records) and state exactly who is authorised to access it. Provide simple instructions on how to store and share this data safely.
When you combine consistent training with practical tests and clear guidelines, you build that robust human firewall. Every single person on your team becomes an active part of your defence, understanding their personal responsibility in protecting the business from the inside out.
Creating Your Simple Incident Response Plan

Let's be realistic: even with the best defences in place, a cyber incident can still happen. The real difference between a minor hiccup and a business-ending disaster often comes down to how you react in those first few critical hours.
Think of an incident response plan as your digital fire escape route. It's a clear set of instructions to follow when things go wrong, helping you minimise damage and restore your operations with confidence, not panic.
For a small business, this plan doesn't need to be a hundred-page thesis. It just needs to be simple, clear, and easy to follow under pressure. The goal is to figure out the ‘what ifs’ before they happen, so your team knows exactly who to call and what to do.
A sobering study of small businesses revealed that a shocking 75% could not continue operating if hit with ransomware. A simple, rehearsed response plan is one of the most effective ways to ensure your business doesn't become part of that statistic.
The Four Stages of Incident Response
A good plan breaks down the chaos of an attack into four manageable stages. It provides a logical sequence for taking back control. Your plan should clearly outline who is responsible for each step and how they’ll communicate with everyone else.
-
Containment: Your immediate priority is to stop the bleed. This means disconnecting affected devices from the network, changing critical passwords, and doing whatever it takes to prevent the problem from spreading.
-
Eradication: Once you've stopped the immediate damage, you need to find the root of the problem and get rid of it for good. This might involve running antivirus scans to eliminate malware or patching the security hole the attacker exploited.
-
Recovery: With the threat gone, it's time to get back to business. This is where you'll restore data from clean backups, rebuild systems from scratch if needed, and monitor everything closely to make sure the threat is truly gone.
-
Lessons Learned: After the dust settles, it’s crucial to review what happened. What went wrong? What actually went right? Use these insights to update your security measures and strengthen your defences to prevent it from happening again.
Building a detailed plan from scratch can feel overwhelming. To help you get started, this ultimate disaster recovery checklist offers practical steps you can adapt for your own business.
For many small businesses, having expert guidance on call is invaluable. This is where looking into outsourced IT support can provide professional help and real peace of mind. Having a clear plan is a cornerstone of robust cybersecurity for small businesses.
Frequently Asked Questions About Small Business Cybersecurity
https://www.youtube.com/embed/aZRhzea_nas
When it comes to cybersecurity, it's completely normal for small business owners to feel a bit overwhelmed. You've got questions, and we've heard them all. Here are our straightforward answers to some of the most common queries we get from businesses just like yours.
How Much Should a Small Business Budget for Cybersecurity?
There's no one-size-fits-all answer, but a good rule of thumb is to set aside somewhere between 3% and 6% of your total IT budget purely for security.
If you're just starting out, don't feel you have to spend a fortune. Focus on the essentials first. A solid anti-malware subscription, a dependable cloud backup service, and some dedicated time for staff training will give you a strong foundation. The trick is to start by figuring out what you need to protect most—your most valuable data and your biggest vulnerabilities. Spend your budget there first, and you can always scale up your security investment as your business grows.
Is Cloud Storage Safer Than Keeping Data On-Site?
For most businesses, the answer is a definite yes. Think about it: major cloud providers like Google, Microsoft, and Amazon pour billions into security measures that are simply out of reach for a small company. They have entire teams of experts, Fort Knox-level physical security, and sophisticated systems all working around the clock to protect their servers.
That said, it's a partnership. They secure their infrastructure (the "cloud"), but you're in charge of securing your access to it. This means using strong, unique passwords, switching on multi-factor authentication (MFA), and being careful about who you give access to. The cloud is incredibly secure, but only when it's used correctly.
Do I Need Cyber Insurance for My Small Business?
These days, cyber insurance is less of a "nice-to-have" and more of an essential safety net. It’s designed to cushion the financial blow from a cyberattack, covering costs like data recovery, legal bills, customer notifications, and even regulatory fines.
It's shocking, but only 17% of small businesses currently have a specific cyber insurance policy, which leaves most companies wide open to serious financial risk. Before you sign up, read the fine print. You need to know exactly what's covered and what's not. Many insurers now insist you have basic security measures, like MFA, in place just to qualify for a policy. Think of it as a crucial part of your overall security plan, not a substitute for it.
At Ibertech Solutions Limited, we specialise in creating secure digital environments for small businesses across Norfolk and Suffolk. From robust website security to comprehensive IT support, we provide the expertise you need to protect your business. Contact us today to strengthen your cybersecurity posture.





