In 2024, demonstrating robust data protection isn't just a legal necessity; it's a cornerstone of customer trust. The General Data Protection Regulation (GDPR) continues to set the global standard for privacy, and non-compliance can lead to severe financial penalties and reputational damage. For small and medium-sized enterprises in Norfolk, Suffolk, and across the UK, the complexity of GDPR can feel overwhelming. However, a structured approach can demystify the requirements and transform compliance from a daunting task into a competitive advantage.
This detailed GDPR compliance checklist provides a step-by-step roadmap, breaking down the eight most critical areas your business must address. We move beyond generic advice to offer specific, actionable guidance tailored for businesses looking to secure their digital operations, whether you're a retailer with a bespoke eCommerce site or a company relying on Microsoft 365 services.
Inside, you will find practical steps for:
- Identifying the correct legal basis for data processing.
- Implementing systems to uphold data subject rights.
- Integrating Privacy by Design into your projects.
- Knowing when and how to conduct a Data Protection Impact Assessment (DPIA).
- Maintaining accurate and compliant data processing records.
- Managing international data transfers legally.
- Developing a solid data breach detection and response plan.
- Ensuring your third-party vendor agreements are GDPR-compliant.
Each point is designed to be a clear, manageable task, helping you build and maintain a compliant and secure digital environment. Let's begin the journey to mastering your data protection responsibilities and turning them into a powerful business asset.
1. Data Processing Legal Basis Identification
The very first step in any robust GDPR compliance checklist is to establish and document a valid legal basis for every single data processing activity your organisation undertakes. Under the GDPR, you cannot simply collect and use personal data because you want to; you must have a specific, lawful reason. This principle is the bedrock upon which all other data protection obligations are built.
Identifying the correct legal basis is critical because it directly influences individuals' rights. For instance, the right to erasure or the right to data portability may not apply depending on the basis you choose. Getting this wrong can undermine your entire compliance framework and lead to significant penalties.
The Six Legal Bases for Processing
The GDPR outlines six potential lawful bases. You must determine which one is most appropriate for each processing activity you perform.
- Consent: The individual has given clear, affirmative permission for you to process their personal data for a specific purpose. This must be freely given, specific, informed, and unambiguous. Understanding the nuances of GDPR consent requirements is essential, as this basis gives data subjects the most control, including the absolute right to withdraw consent at any time.
- Contract: Processing is necessary for a contract you have with the individual, or because they have asked you to take specific steps before entering into a contract. For example, processing a customer's address to deliver an online order.
- Legal Obligation: Processing is necessary for you to comply with the law (not including contractual obligations). This could involve sharing employee salary data with HMRC.
- Vital Interests: Processing is necessary to protect someone’s life. This is rare and typically applies to emergency medical situations.
- Public Task: Processing is necessary for you to perform a task in the public interest or for your official functions, and the task or function has a clear basis in law. This is most relevant for public authorities.
- Legitimate Interests: Processing is necessary for your legitimate interests or the legitimate interests of a third party, unless there is a good reason to protect the individual’s personal data which overrides those legitimate interests.
Key Insight: Choosing a legal basis is not a one-time decision. You must document it from the start and review it regularly, especially if your purposes for processing data change. You generally cannot swap to a different legal basis later if your initial choice proves inappropriate.
Practical Implementation
To put this into action, create a "Record of Processing Activities" (ROPA). This document, often a detailed spreadsheet, should map every type of data you process (e.g., customer emails, employee HR files) to its specific purpose and its corresponding legal basis.
- Example 1 (Contract): An eCommerce retailer processes a customer’s name, address, and payment details. The legal basis is Contract, as this is necessary to fulfil the order.
- Example 2 (Legitimate Interests): A B2B service provider analyses anonymised user interaction data within its software to identify and fix bugs. The legal basis could be Legitimate Interests (to improve the product), provided it doesn't override user privacy rights. This requires a formal Legitimate Interests Assessment (LIA) to be conducted and documented.
- Example 3 (Consent): The same retailer asks customers if they want to sign up for a weekly marketing newsletter. The legal basis for sending these emails is Consent.
2. Data Subject Rights Implementation
A core component of any GDPR compliance checklist is building a clear and efficient framework for handling data subject rights. The GDPR empowers individuals with significant control over their personal data, granting them eight fundamental rights. Your organisation must not only be aware of these rights but also have robust procedures in place to honour them promptly and effectively.

Failing to manage these requests can lead to direct complaints to supervisory authorities like the ICO, damaging your reputation and risking financial penalties. A well-organised system demonstrates respect for customer privacy and is a tangible sign of your commitment to data protection. You are required to respond to requests without undue delay, and at the latest within one month.
The Eight Fundamental Rights
Your procedures must be equipped to handle each of the rights granted to individuals. It is crucial your staff, especially customer-facing teams, can recognise and correctly action these requests.
- The right to be informed: Individuals must be told how their data is collected, used, and stored, typically via a privacy notice.
- The right of access: Individuals can request a copy of their personal data, commonly known as a Subject Access Request (SAR).
- The right to rectification: Individuals can have inaccurate or incomplete personal data corrected.
- The right to erasure: Also known as 'the right to be forgotten', allowing individuals to have their data deleted in certain circumstances.
- The right to restrict processing: Individuals can request to limit the way your organisation uses their data.
- The right to data portability: Allows individuals to obtain and reuse their personal data for their own purposes across different services.
- The right to object: Individuals can object to the processing of their personal data in specific situations, such as for direct marketing.
- Rights in relation to automated decision making and profiling: Individuals have rights to safeguards against potentially damaging decisions made without human intervention.
Key Insight: While you must respond within one month, this can be extended by a further two months for complex or numerous requests. However, you must inform the individual of this extension within the first month and explain the reasons for the delay. Most requests must be handled free of charge.
Practical Implementation
Your goal is to make the process as straightforward as possible for both the individual and your team. A combination of automated tools and clear internal policies is the most effective approach.
- Example 1 (Automation): Apple’s privacy portal is a prime example of effective implementation. It allows users to self-serve, letting them download a complete copy of their data, request corrections, or permanently delete their account with minimal staff intervention.
- Example 2 (Clear Process): Your business should have a designated email address (e.g., [email protected]) and a web form for submitting requests. This centralises all incoming queries, ensuring none are missed.
- Example 3 (Internal Training): Train your customer service team to identify a data subject request, regardless of how it is phrased. They need a clear procedure for verifying the individual's identity and escalating the request to the correct person or department for fulfilment. A detailed log of every request received and the actions taken is mandatory for accountability.
3. Privacy by Design and Default Implementation
A core principle of the GDPR is to shift data protection from a reactive, damage-control exercise to a proactive, foundational element of your operations. This is the essence of Privacy by Design and by Default. It mandates that organisations embed data privacy considerations into the very fabric of their projects, technologies, and business practices right from the beginning, rather than attempting to add them on later.

This approach is not just a recommendation; it's a legal requirement under Article 25 of the GDPR. Privacy by Design means you consider data protection at the earliest stages of any new project. Privacy by Default ensures that when a system or service is released, the most privacy-friendly settings are the default, meaning users don't have to search for them to protect their data.
The Two Pillars of Proactive Privacy
Understanding these two interconnected concepts is vital for any modern business handling personal data. They form a crucial part of a comprehensive GDPR compliance checklist.
- Privacy by Design: This is the process of integrating data protection measures into the design of your processing activities and business practices. It means conducting Privacy Impact Assessments (PIAs) before you launch a new product, using privacy-enhancing technologies like encryption, and ensuring your development lifecycle includes privacy checkpoints. The goal is to anticipate and prevent privacy risks before they can materialise.
- Privacy by Default: This principle requires that you only process the data that is absolutely necessary for each specific purpose (data minimisation). It also means that, by default, personal data is not made accessible to an indefinite number of people without the individual's intervention. For example, social media profile settings should default to private, not public.
Key Insight: Implementing Privacy by Design and Default is about making privacy the standard setting. It demonstrates a commitment to data protection that builds trust with your customers and regulators, proving that you see privacy as an integral part of your service, not a burdensome obligation.
Practical Implementation
Integrating this principle requires a cultural shift towards a privacy-first mindset. It should be a continuous process, not a one-off task.
- Example 1 (Privacy by Design): The messaging app Signal was built from the ground up with end-to-end encryption and minimal data collection as core features, not optional add-ons. They designed the system so that they, the service provider, could not access user communications.
- Example 2 (Privacy by Default): A new mobile app asks for location access. Instead of defaulting to "Always On," the most privacy-protective setting would be "Only While Using the App" or "Ask Every Time." The user must actively choose to provide more data.
- Example 3 (Data Minimisation): An online registration form for a webinar should only ask for a name and email address. By default, it should not include optional, non-essential fields for phone number, company size, or job title, as this data is not necessary for the purpose of webinar access.
4. Data Protection Impact Assessment (DPIA) Process
A core component of any thorough GDPR compliance checklist is establishing a formal process for conducting Data Protection Impact Assessments (DPIAs). A DPIA is a mandatory risk assessment required under the GDPR whenever a processing activity is likely to result in a high risk to the rights and freedoms of individuals. It is a systematic process for identifying and minimising data protection risks before a project begins.
Conducting a DPIA is not just a box-ticking exercise; it is a fundamental part of the GDPR's accountability principle. It forces an organisation to think carefully about the necessity and proportionality of its data processing activities, particularly when deploying new technologies, processing sensitive data on a large scale, or systematically monitoring individuals.
When a DPIA is Required
You must conduct a DPIA before you begin any processing that is likely to be high risk. The GDPR specifically highlights several scenarios where a DPIA is mandatory:
- Systematic and Extensive Evaluation: When you use automated processing, including profiling, to make decisions that have legal or similarly significant effects on people. For example, an automated credit scoring system.
- Large-Scale Processing of Special Categories: Processing sensitive personal data (e.g., health, biometrics, race, political opinions) on a large scale. The NHS conducting DPIAs for its COVID-19 contact tracing app is a prime example.
- Systematic Monitoring of a Publicly Accessible Area: Large-scale monitoring of public spaces, such as using CCTV across a city centre.
Key Insight: A DPIA is a proactive, not a reactive, tool. It must be completed before the processing starts. If a DPIA identifies high risks that you cannot mitigate, you are legally required to consult with your supervisory authority (the ICO in the UK) before proceeding.
Practical Implementation
Integrating DPIAs into your project lifecycle is crucial for maintaining compliance. A standardised approach ensures consistency and thoroughness across all relevant projects.
- Example 1 (Biometrics): Uber conducted extensive DPIAs before launching a facial recognition system to verify its drivers’ identities. The assessment would have evaluated risks related to data security, accuracy, and potential for discrimination, leading to measures to protect drivers.
- Example 2 (AI): A financial institution planning to use a new AI-powered system for fraud detection must conduct a DPIA. This assesses the risks of inaccurate profiling, the fairness of the algorithm, and the impact on customers, ensuring mitigation measures are in place.
The following infographic illustrates the fundamental workflow of a DPIA.
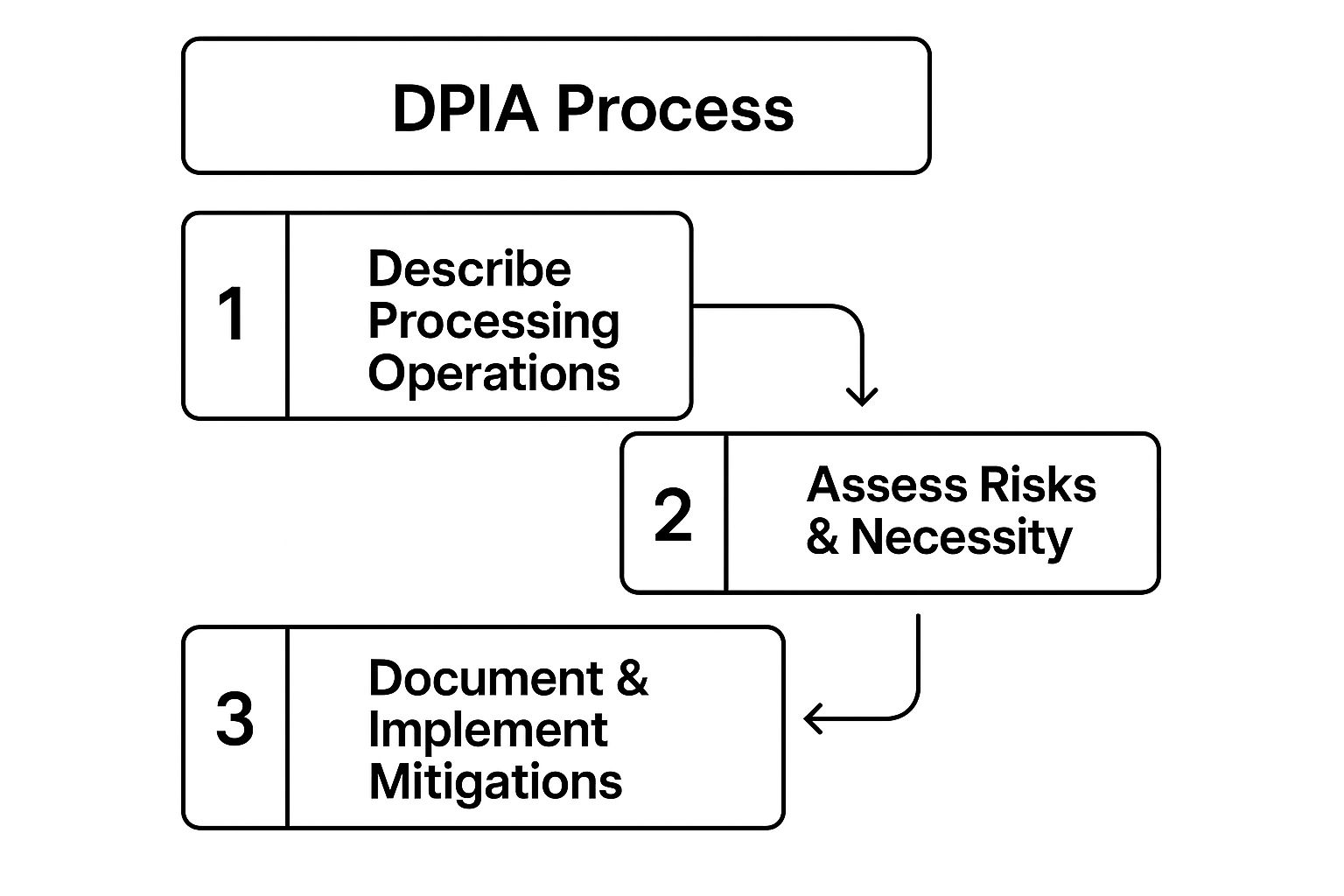
This process flow highlights that a DPIA is a structured journey, starting with a clear description of the processing, moving to a detailed risk assessment, and concluding with actionable mitigation plans. Combining this process with a wider evaluation, such as through a cyber security assessment, can provide a comprehensive view of your organisational risk posture.
5. Data Processing Records and Documentation
A core tenet of GDPR accountability is the ability to demonstrate compliance, and this is impossible without meticulous record-keeping. While mandatory for organisations with over 250 employees or those engaged in high-risk processing, maintaining a detailed Record of Processing Activities (ROPA) is a best practice for all. This documentation acts as a central inventory of your data flows, providing a clear map of what personal data you handle, why you handle it, and how you protect it.
A well-maintained ROPA is not just a compliance document; it is a critical operational tool. It enables you to respond efficiently to data subject requests, conduct data protection impact assessments (DPIAs), and manage potential data breaches. Without it, understanding your own data ecosystem becomes a significant, time-consuming challenge, especially when under pressure.
What to Include in Your ROPA
Article 30 of the GDPR specifies the information that must be included in your processing records. Your documentation should be comprehensive and readily available for inspection by a supervisory authority like the ICO.
- Controller & DPO Details: Name and contact details of your organisation (the controller) and, where applicable, your Data Protection Officer (DPO).
- Purposes of Processing: A clear description of why you are processing the data (e.g., fulfilling customer orders, sending marketing emails, managing payroll).
- Data Categories: The types of individuals (data subjects) and the categories of personal data being processed (e.g., customer names and contact details, employee financial information).
- Data Recipients: Any third parties or categories of recipients with whom the personal data is shared, including those in other countries.
- International Transfers: Details of any data transfers to countries outside the UK/EEA and the safeguards in place for these transfers.
- Retention Schedules: The envisaged time limits for the erasure of different categories of data.
- Security Measures: A general description of the technical and organisational security measures implemented to protect the data (e.g., encryption, access controls, staff training).
Key Insight: Treat your ROPA as a living document. It should be integrated into your business-as-usual processes. Whenever a new project is initiated that involves personal data, updating the ROPA should be a mandatory step in the project's approval gateway.
Practical Implementation
Start by using a spreadsheet or a dedicated GDPR compliance tool to create your ROPA. Systematically work through each department to map their data processing activities.
- Example 1 (Retail): A company like Airbnb must document the processing of host and guest data. Its ROPA would detail purposes like identity verification, payment processing, and review management, noting the categories of data (ID documents, financial details), recipients (payment processors), and varied retention periods.
- Example 2 (Finance): Banks maintain incredibly detailed ROPAs covering every financial product. For a mortgage application, the record would list the purpose (credit assessment), data categories (income, credit history), recipients (credit reference agencies), and long-term retention schedules mandated by financial regulations.
- Example 3 (Tech): A service like Spotify documents the processing of user data for purposes such as personalising playlists (legitimate interest) and serving targeted ads (consent), detailing the data categories (listening history, location data) and the security measures protecting them.
6. International Data Transfer Compliance
A crucial part of any comprehensive GDPR compliance checklist involves managing the transfer of personal data outside the European Economic Area (EEA). The GDPR places strict controls on these "international transfers" to ensure that the high standard of data protection afforded to individuals within the EEA is not undermined when their data is sent abroad. You cannot simply transfer data to a third country or international organisation; you must ensure it remains protected.
Failing to correctly manage international data transfers is a major compliance risk, highlighted by landmark legal cases like Schrems II. This ruling invalidated the EU-US Privacy Shield and reinforced the obligation on data exporters to verify, on a case-by-case basis, that the recipient country’s laws provide protection essentially equivalent to that in the EU.
Mechanisms for Lawful International Transfers
The GDPR provides several mechanisms to legitimise international data transfers. You must implement one of these before any data leaves the EEA.
- Adequacy Decision: The European Commission can formally decide that a third country provides an adequate level of data protection. Transfers to these countries (like the UK, Switzerland, or Japan) are permitted without any further specific authorisation.
- Appropriate Safeguards: If no adequacy decision exists, you must put in place appropriate safeguards. The most common of these are Standard Contractual Clauses (SCCs), which are model data protection clauses adopted by the Commission. Other safeguards include Binding Corporate Rules (BCRs) for multinational corporate groups.
- Derogations: In specific, non-repetitive situations, transfers can be made based on derogations. These include explicit consent from the individual for the specific transfer, or if the transfer is necessary for a contract or for vital interests. These are exceptions and should not be used for routine transfers.
Key Insight: Simply signing Standard Contractual Clauses (SCCs) is no longer enough. Following the Schrems II ruling, organisations must also conduct and document a Transfer Impact Assessment (TIA) to evaluate whether the SCCs can be complied with in practice in the destination country. If not, supplementary measures are required.
Practical Implementation
Your primary task is to map all data flows to identify any that leave the EEA, then apply the correct transfer mechanism.
- Example 1 (Standard Contractual Clauses): A UK-based marketing firm uses a US-based email automation platform. Since the US does not have an adequacy decision (though the EU-US Data Privacy Framework exists for certified companies), the firm must sign SCCs with the provider. It must also conduct a TIA and implement supplementary measures, such as end-to-end encryption, to protect the data from potential access by US public authorities.
- Example 2 (Adequacy): A British retailer uses a customer service centre located in the UK. When sharing customer data with this centre, no specific international transfer mechanism is needed as the UK has an adequacy decision from the EU.
- Example 3 (Data Localisation): To avoid the complexities of TIAs, a tech company like Zoom reconfigured its architecture to ensure all European customer data is processed and stored exclusively in its EU-based data centres, thereby avoiding an international transfer altogether.
Understanding how these rules affect your digital presence is vital; explore our comprehensive website compliance checklist for more details.
7. Data Breach Detection and Response Plan
A critical component of any GDPR compliance checklist is having a robust, well-documented plan for detecting and responding to personal data breaches. It's not enough to simply try and prevent breaches; you must be prepared to act swiftly and effectively when one occurs. Under the GDPR, the clock starts ticking the moment you become aware of a potential incident, with strict deadlines for reporting to authorities and notifying individuals.

Failing to manage a breach correctly can drastically amplify the consequences, leading to severe regulatory fines and catastrophic damage to your reputation. A structured response plan ensures you meet legal obligations, mitigate harm to data subjects, and demonstrate accountability to regulators. It transforms a chaotic crisis into a managed process. For more information on preventative measures, you can learn more about cybersecurity for small businesses.
The Breach Notification Timelines
The GDPR sets out clear timeframes for notification that every organisation must adhere to. Understanding these is fundamental to your response plan.
- Report to Supervisory Authority: You must report a personal data breach to the relevant supervisory authority (like the UK's ICO) within 72 hours of becoming aware of it, unless the breach is unlikely to result in a risk to the rights and freedoms of individuals.
- Inform Affected Individuals: If the breach is likely to result in a high risk to the rights and freedoms of individuals, you must inform those affected directly and "without undue delay."
Key Insight: "Becoming aware" means the moment you have a reasonable degree of certainty that a security incident has occurred and that it has compromised personal data. Don't delay your 72-hour countdown while you conduct a full investigation; the clock starts as soon as you have initial awareness.
Practical Implementation
Your response plan must be a practical, actionable document, not a theoretical exercise. It should clearly outline the steps to take from detection to resolution.
- Example 1 (Delayed Notification): Marriott International was fined £18.4 million by the ICO. A key factor in the penalty was the significant delay between the discovery of a major data breach and its notification to both regulators and the affected customers, highlighting the cost of a slow response.
- Example 2 (Inadequate Security): British Airways faced a £20 million fine after a cyber-attack compromised the data of over 400,000 customers. The ICO cited inadequate security measures and a failure to protect customer data effectively as central to their decision, showing that prevention and response are two sides of the same coin.
- Example 3 (Proactive Response): When Twitter experienced a breach in 2020, its prompt notification and transparent communication with both users and regulators were viewed favourably, demonstrating how a well-executed response can help manage reputational damage even in a crisis.
8. Vendor and Third-Party Data Processing Agreements
Your organisation's GDPR responsibility does not end at your own digital doorstep. If you use any third-party service to process personal data on your behalf, from cloud hosting providers to email marketing platforms, you are legally obligated to ensure they also meet GDPR standards. The GDPR holds you, the data controller, liable for the actions of your data processors, making this a critical part of any gdpr compliance checklist.
This is managed through a specific legal contract known as a Data Processing Agreement (DPA). A DPA is a non-negotiable requirement under Article 28 of the GDPR. It contractually binds your vendor to protect the data you entrust to them, follow your instructions explicitly, and uphold the rights of data subjects. Without a robust DPA in place for every single vendor processing personal data, your compliance framework has a significant and costly gap.
The Core Components of a DPA
A compliant DPA is not a simple tick-box exercise; it must be a detailed document that clearly outlines the responsibilities of both the controller (you) and the processor (your vendor).
- Subject Matter and Instructions: The DPA must specify the subject matter, duration, nature, and purpose of the processing, as well as the types of personal data and categories of data subjects involved. Crucially, it must state that the processor will only act on your documented instructions.
- Confidentiality: The vendor must commit to ensuring that any staff authorised to process the data are bound by a duty of confidentiality.
- Security Measures: The processor must implement appropriate technical and organisational measures to ensure the security of the data, as outlined in Article 32 of the GDPR. This includes encryption, access controls, and resilience testing.
- Sub-processing: The vendor cannot engage another processor (a sub-processor) without your prior written authorisation. The DPA must outline this process, and the same data protection obligations must be passed down to any sub-processor.
- Data Subject Rights: The processor must assist you in responding to requests from individuals exercising their GDPR rights (e.g., access, rectification, erasure).
- Breach Notification: The vendor must notify you "without undue delay" after becoming aware of a personal data breach, enabling you to meet your own reporting obligations.
- Audit and Deletion: The agreement must allow for and contribute to audits conducted by you or an auditor you appoint. It must also detail the procedures for returning or deleting all personal data at the end of the service contract.
Key Insight: A vendor simply stating they are "GDPR compliant" on their website is not enough. You must have a signed, legally-binding Data Processing Agreement that covers all the specific requirements of Article 28. This contract is your primary tool for demonstrating due diligence.
Practical Implementation
Start by creating an inventory of all your third-party vendors. For each one, determine if they process personal data on your behalf. If they do, you must ensure a DPA is in place.
- Example 1 (SaaS Provider): You use a CRM platform like Salesforce to manage customer information. You must sign Salesforce's DPA, which outlines their security commitments and how they will handle your customer data according to GDPR rules.
- Example 2 (Cloud Host): Your website and its database are hosted on AWS. You must accept AWS's Data Processing Addendum, which forms part of your service agreement and details their compliance certifications and security infrastructure.
- Example 3 (Marketing Agency): You hire an external agency to run your email marketing campaigns. You must have a bespoke DPA with the agency that explicitly details what data they can use, for what purpose (your campaigns), and their security obligations.
8-Point GDPR Compliance Checklist Comparison
| Item | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases 💡 | Key Advantages ⭐ |
|---|---|---|---|---|---|
| Data Processing Legal Basis Identification | High – requires detailed legal assessment per activity | Moderate – legal and compliance expertise needed | Clear lawful foundation for data use | All processing activities under GDPR | Reduces legal risks; establishes subject rights |
| Data Subject Rights Implementation | High – complex workflows and technical integration | High – automation, verification systems | Empowered individuals; improved trust | Handling data access, deletion, portability | Builds transparency; competitive privacy leadership |
| Privacy by Design and Default Implementation | High – design integration from project start | High – privacy experts, development time | Proactive privacy protection built-in | New products, systems requiring privacy by default | Cost-effective long term; stronger trust |
| Data Protection Impact Assessment (DPIA) Process | Moderate to high – systematic risk assessment required | High – privacy expertise and stakeholder involvement | Early risk identification and mitigation | High-risk or innovative processing | Demonstrates compliance; reduces violations |
| Data Processing Records and Documentation | Moderate – ongoing documentation and updates | Moderate – administrative effort | Comprehensive process visibility | Organizations with 250+ employees or high-risk processing | Facilitates audits and incident response |
| International Data Transfer Compliance | High – complex legal and technical assessments | High – legal, technical safeguards | Ensured lawful international data transfers | Transfers outside EU/EEA | Enables global operations; standardized safeguards |
| Data Breach Detection and Response Plan | High – 24/7 monitoring and rapid response | High – monitoring tools and trained staff | Minimized breach impact; regulatory compliance | Incident response and breach management | Preserves trust; reduces penalties |
| Vendor and Third-Party Data Processing Agreements | Moderate to high – legal negotiations and monitoring | Moderate to high – contract management | Ensures processor compliance and liability | Engagement with data processors | Clarifies roles; legal and compliance control |
Embedding Privacy into Your Business DNA
Navigating the intricacies of the General Data Protection Regulation can feel like a monumental task, especially for small and medium-sized businesses. The comprehensive GDPR compliance checklist we have explored throughout this article provides a structured pathway, demystifying what is often perceived as a complex web of legal obligations. By methodically addressing each point, from establishing a lawful basis for processing to formalising data processing agreements with your vendors, you have laid a robust foundation for regulatory adherence.
However, the journey doesn't end once you've ticked the final box. True, lasting compliance is not a static achievement but a dynamic, ongoing commitment. It's about shifting from a reactive, task-based approach to proactively embedding a culture of privacy deep within your organisation's DNA. This cultural shift transforms GDPR from a regulatory burden into a framework for building and maintaining customer trust, which is arguably one of the most valuable assets in today's digital economy.
From Checklist to Culture: Key Takeaways
To ensure your efforts have a lasting impact, let's crystallise the core principles that transcend the checklist itself:
- Accountability is Non-Negotiable: The principle of accountability, woven throughout the GDPR, means you must not only comply but also be able to demonstrate your compliance. Maintaining meticulous records of processing activities (ROPA), documenting your DPIAs, and keeping your data breach response plan updated are tangible proofs of your commitment.
- Privacy by Design is Proactive, Not Reactive: Implementing Privacy by Design and Default isn't just a technical requirement; it's a strategic mindset. It means considering data protection implications at the outset of any new project, product, or business process. This proactive stance is far more efficient and effective than trying to bolt on privacy features after the fact.
- Data Subject Rights are Your Customers' Rights: Honouring data subject rights, such as the right to access, rectify, or erase their data, is fundamental. A transparent and efficient process for handling these requests doesn't just satisfy a legal requirement; it shows your customers you respect their autonomy and value their trust.
Actionable Next Steps for Sustained Compliance
Completing the initial GDPR compliance checklist is a significant milestone. Now, the focus must shift to maintenance and continuous improvement. Here are your immediate next steps to ensure your organisation remains compliant and resilient:
- Schedule Regular Reviews: Diarise quarterly or biannual reviews of all your GDPR documentation and processes. Are your data maps still accurate? Are your privacy notices still clear and up-to-date? This regular cadence ensures your compliance framework evolves with your business.
- Implement Ongoing Staff Training: A single training session is not enough. Develop a programme of continuous education to keep all employees, from the marketing team in Norwich to the IT support staff in Ipswich, aware of their responsibilities. Use real-world scenarios relevant to their roles to make the training engaging and memorable.
- Monitor Regulatory Updates: The data protection landscape is not static. Supervisory authorities like the Information Commissioner's Office (ICO) regularly issue new guidance. Appoint someone to monitor these updates and assess their impact on your operations, ensuring your policies and procedures remain current.
By treating data protection as an integral part of your business strategy, you move beyond mere compliance. You build a reputation for integrity and responsibility that can differentiate you from competitors and foster deep, long-lasting relationships with your customers. This journey from a paper-based exercise to a living, breathing part of your company culture is the ultimate goal, turning a legal necessity into a powerful business advantage.
Navigating the technical side of your GDPR compliance checklist, from secure web hosting to implementing robust website security, can be a major hurdle. Let the experts at Ibertech Solutions Limited provide the tailored IT support and digital marketing services your East Anglian business needs to thrive securely. Contact us today to learn how we can help you build a compliant and trusted online presence.





